Quantum Random Number Generator: Difference between revisions
Tag: Manual revert |
|||
| Line 35: | Line 35: | ||
== Principles == | == Principles == | ||
[[File: | [[File:Principle schematic of QRNG.png|thumb|400px| Principle schematic of QRNG]] | ||
In cybersecurity, a perfect random number is the root of trust. A QRNG does not rely on mathematical algorithms but on laws of quantum physics to ‘naturally’ generate random numbers. | In cybersecurity, a perfect random number is the root of trust. A QRNG does not rely on mathematical algorithms but on laws of quantum physics to ‘naturally’ generate random numbers. | ||
Revision as of 03:10, 23 April 2022
Team Members
Wang Yang A0228753X
Xiao Yucan A0236278W
Zhang Munan A0236273E
Idea
We live in an increasingly connected world, where a superior source of entropy is the key to data security. The effectiveness of any cryptographic system is determined by the strength of the keys it used. In turn, the strength of the key is determined by the degree of randomness used in its generation. And Quantum Random Number Generators (QRNGs) leverage the random properties of quantum physics to generate a true source of entropy, improving the quality of seed content for key generation.
- BENEFITS OF HAVING A QUANTUM RANDOM NUMBER GENERATOR:
- The source of randomness is unpredictable and controlled by quantum process.
- The entropy source tends to produce true random output.
- Live/ real-time monitoring of entropy source is possible and highly effective as well.
- All attacks on the entropy source are detectable.
- The above factors indicate that our QRNG is provably secure.
- APPLICATIONS OF QUANTUM RANDOM NUMBER GENERATOR:
- Securing data at rest in data centres
- Securing any kind of sensitive data
- Securing data in the cloud
- One-time pad for authentication in banking and other transactions
- Gaming applications and lottery
- Block-chain network
- Numerical simulations, statistical research
- IoT devices
- E-commerce and banking applications
- Cryptographic applications
- Telecom and 5G
In today’s Y2Q world, developers have to rely on the source of entropy as quantum-enabled security keys are set to become the new normal. Organisations should, therefore, implement QRNG to protect their customers’ data.
Principles
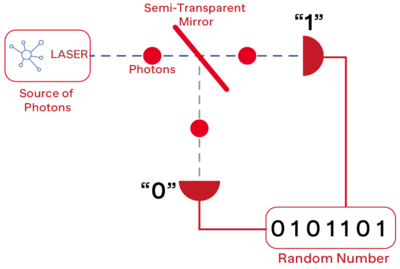
In cybersecurity, a perfect random number is the root of trust. A QRNG does not rely on mathematical algorithms but on laws of quantum physics to ‘naturally’ generate random numbers.
A QRNG can produce unpredictable outcomes in a robust and well-controlled way. It includes the power of complex deep-tech technologies such as semiconductors, optoelectronics, high precision electronics, and quantum physics that work together to create the highest level of randomness possible.
QRNGs use random properties of quantum physics to generate a true source of entropy. This improves the quality of seed for key generation. Since the entropy sources are derived from fundamental models, all the properties and behaviors are understandable and provably secure.
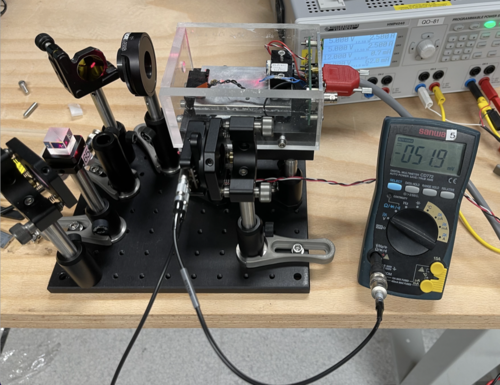
Setup
Gallery
- 26 February 2022:
- 5 March 2022:
- 12 March 2022:
- 19 March 2022:
- 26 March 2022:
- 2 April 2022:
- 9 April 2022:
- 16 April 2022:
* * * Record experimental data.
- 23 April 2022:
* Processing experimental data * Draw autocorrelation images * Summarize and upload the experimental results
Background reading
[1]Quantum random number generators, Miguel Herrero-Collantes and Juan Carlos Garcia-Escartin, Rev. Mod. Phys. 89, 015004.